Welcome to the Janison Academy help portal
Settings
A Role is a collection of rights that can be assigned to Users and determines what they can see and do in the system. Users have one Main Role and they may be allocated a number of Extra Roles that give them rights over particular entities in the CLS. Users never see more functions than they need to use. For example, someone with the additional Marker Role can mark Tests but can’t change Courses and Enrolments or manage Users. A User with a System Administrator Role can do and see everything.
The Security Manager Plugin provides a set of User Interface screens for an administrator and other authorised people to configure Roles to manage access controls.
Managing Roles in the system is not a trivial task, and will usually be completed by the Janison Client Services team.
Roles are managed through Settings > Roles.
The CLS has some fundamental rules in order to maintain data integrity around the enforcement of Security.
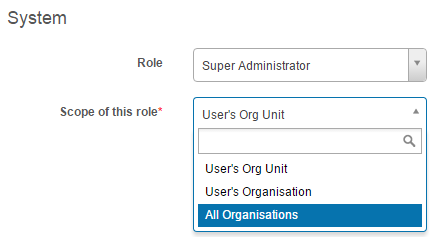
Security Scopes imply that there’s a hierarchy of Entities. There are several access-control hierarchies in the Janison CLS.
That means that Content and People are organised hierarchically around key Securable Entities, and permissions and access flow around this.
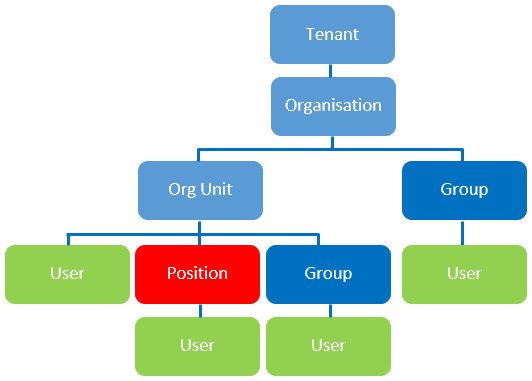
The diagram below shows the Janison CLS People Security Hierarchy.
The diagram below shows the Content Security Hierarchy in the Janison CLS.
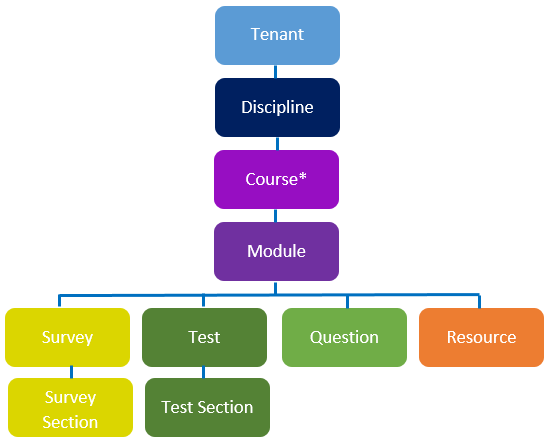
*Courses are only relevant for Learning Modules. See the document on Modules for an explanation on the difference between modules.
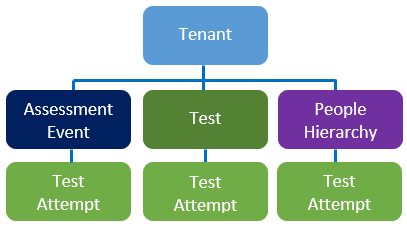
The Diagram below shows the Assessment Event Security Hierarchy.

Menu Items and Buttons are automatically hidden for users who do not have access to them. This is a design choice aimed at achieving simplicity, and ensuring that every user is presented with the least amount of clutter possible.
The List of Roles is located under Settings > Roles.
On this page you can:
 icon.
icon.
Each Role form consists of a top section and several other expandable sections as seen in the screenshot below.
To inspect a role navigate to Settings > Roles and select a Role. We will look at each section in detail in the following topics.


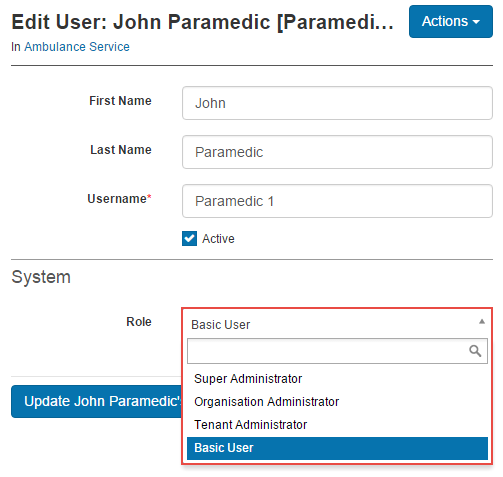
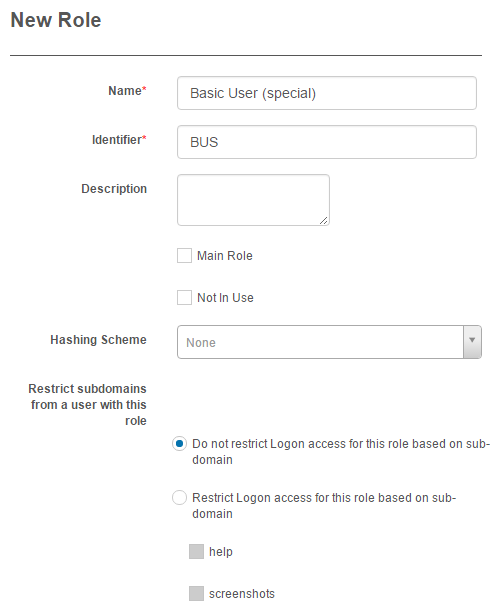
In this section you can view and edit the below fields.
This Section provides a link to all the Users with this Role Assigned to them.



If this option is checked the Role will appear in the drop-down in the System section of the User edit form. This means that the Role can be set as a Main Role for Users on the site.

If this option is checked the Role will become Inactive.
Hashing schemes are used to secure passwords. Any passwords that are stored in the database can be stolen if the database is compromised. By applying a hashing algorithm to passwords, it makes it improbable for any attacker to determine the original password.
Several hashing schemes are available and can be set per Role.

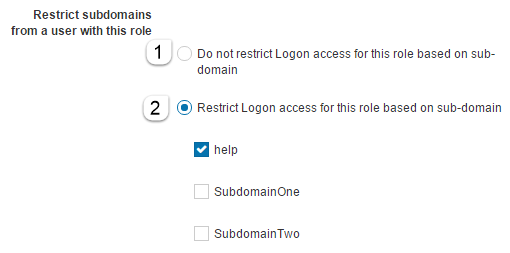
You are not allowed to login through this sub-domain.

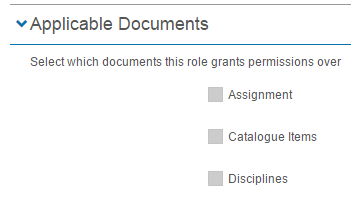
This section allows you to specify the entities/documents that appear in the Role drop-down of the Administrators widget.
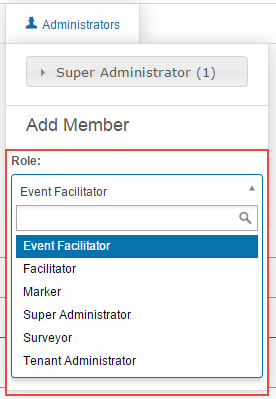
To Edit Applicable Documents:
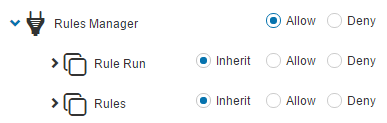
This sections allows you to specify what a User with the Role assigned to them can see and do in the system.

This section has 4 columns:
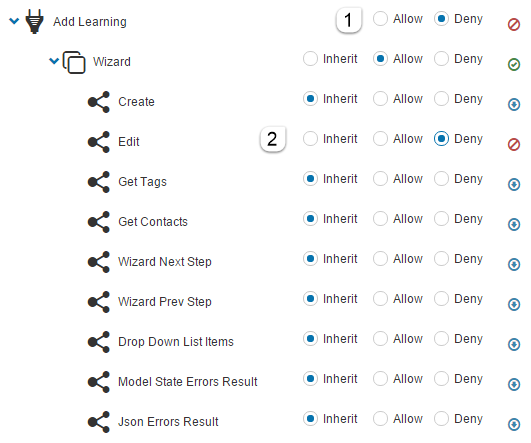
Area – this lists the areas of the CLS where the permissions relate to. It can contain one or more sub areas with child values. The below screenshot lists the Add Learning feature of the system. It has a sub area of Wizard and child values of relating to the Wizard of Create and Edit.

Access – Is the value of the Area and could be:
Effective – To make it obvious what the inherited value is, this column lists the actual values. For example if the parent Area is set to Allow, the Access column will list Inherit whereas the Effective column will list the actual value of Allow.
Indicator – There are three indicator icons to help you quickly understand the values of the Areas settings.
 Users with this Role are allowed in this area of the system.
Users with this Role are allowed in this area of the system.
 Users with this Role are not permitted in this area of the system.
Users with this Role are not permitted in this area of the system.
 Users with this Role are allowed in some Areas and not allowed in other parts of this area of the system.
Users with this Role are allowed in some Areas and not allowed in other parts of this area of the system.
The below screenshot is of the Basic User Role. Three areas are highlighted as examples of different types of access:
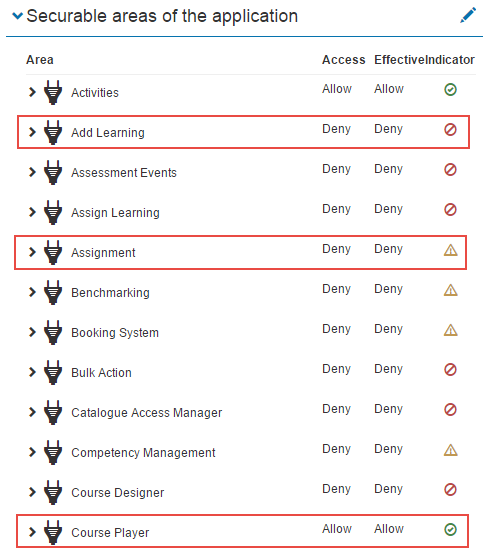
Add Learning is set to Deny as a basic user undertakes learning but does not Add Learning to the system. They therefore do not require access to this part of the system.
Assignment is set to Mixed as Basic Users will only need access to parts of the Assignment feature. For example a Basic User may be required to submit an Assignment so Learner Submission will be set to Allow. They will not be required to Create or Edit an Assignment so these areas will be set to Deny. The basic User therefore has Mixed Access to Assignments.
Course Player is set to Allow as Basic Users require access to the course player to undertake courses.
By editing a Role you can add or remove User access to Areas of the CLS.
To edit Securable areas click the edit pencil of the Roles section.
In the below example a Content Designer Extra Role has been set to Allow Add Learning but will not be permitted to edit the Learning once created.
Although some Areas are easily identifiable such as Add Learning, others are more challenging to find.
As an example, say you need to provide a Tenant Administrator’s access to create User Enrolment Rules. Nothing in the Areas column has this label. To determine the correct Area to specify these step may assist:

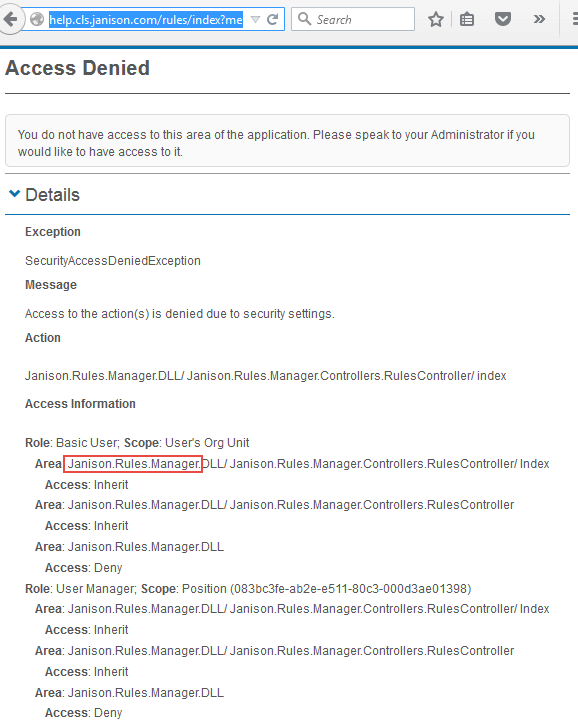
You now know the Area to Allow. It would be advisable to copy the setting configuration of the Role with access to the Area.
Role restrictions allow you to set specific times and durations when Users can access the system.

This option will not restrict access to the system.

Users in this role have access to the system only at specific times for specific durations
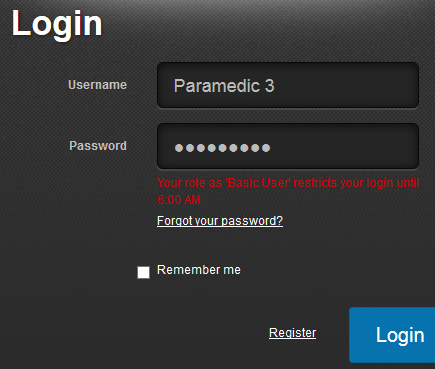
If this setting is active you will need to set an Earliest logon time and a Force log off at time. In the below example it will not be possible for Users to logon before 6 AM and they will be forced to log off at 6.30 PM.

If a User attempts to access the system outside of these hours the message, Your role as ‘Basic User’ restricts your login until 6:00 AM. or similar will be encountered.
Checking this box will override the restrictions on weekends.

This section has the functionality for Administrators to compare a selected Role to other Roles in 3 different ways:
Actions allowed in other roles but not in this role.
Actions denied in other roles but not in this role.
Actions in other roles with effective access different to one in this role.

In the below example we have opened the Basic User Role and have clicked the Actions allowed in other roles but not in this role link. By doing this we are going to determine what additional access any other roles has compared to the Basic User. In this example we are looking at the Content Designer Role. When Expanding Areas of the Role, we can see all the Areas the Content Designer has access to which the Basic User does not. For example Content Designer has access to the Asset Browser and File browser. The Basic User does not have access to these Areas.

If we open the Super Administrator Role and expanded the Actions allowed in other roles but not in this role link, there would be nothing listed in any of the other Roles as the Super Administrator Role has full permissions to every feature available in the system.
The Menu section displays the menu items a user logged in with that particular Role will see.
The first screenshot below is the Menu section of the Basic User Role. Only few menu items are listed compared to the Role in the second screenshot.

The below screenshot is the Menu section of the Tenant Administrator Role. Many more menu items than in the Basic User Role are listed.

The Janison CLS ships with a number of in-built roles, however, it’s possible to create additional roles for flexibility purposes. This requires 3 steps:
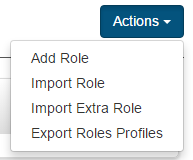
The Janison CLS provides Role Definition Export and Import tools, facilitating the sharing of common or standard role configurations between tenants.
The Export function for a role will generate an XML definition containing all the security tokens (i.e. statements about whether or not the given role is allowed a particular right). This function is mainly used by Janison staff to update the CLS product with new Roles containing in-built Role configurations.

The User Extra Roles Widget provides the ability for authorised Users to view and manage extra roles for a given User directly from the User’s profile. The widget is available from the User detail screen only.
The Widget is divided into 2 sections:

In the screenshot above the Main Role of the User is Basic User. The User is only required to be the marker for certain Learning Assets. Setting them as a Marker as their Main Role would give them access to mark all learning on the site. Applying the Marker Role as an Extra Role limits their access to mark only the stipulated Learning Assets.

Another example for the use of the widget could be to set a Content Designer for a discipline.
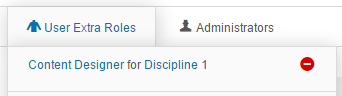
This would give them access to the Design Menu and anything related to the Discipline they are assigned to. In this example Discipline 1.
Finding the correct rights to assign to a user may take some trial end error. Here are some steps you can take to help you achieve the required outcome.
The Administrators Widget provides the ability for authorised Users to view and manage extra roles for one or more Users from within the scope of the Entity it is configured in. The widget is available on all Details forms for Securable Entity Types as listed below.
The Widget is divided into 2 sections:

The Administrators widget is similar to the User extra roles widget in what it achieves but it does it within the scope of the Entity it is configured from. For example, in the screenshot above a User has been assigned a Role of Marker from within a Discipline. That user can therefore only be assigned tests to mark that were created in that particular discipline.
The Janison CLS enforces a business rule where one user can never edit another user that has more rights. For example, a Content Administrator would not be able to edit the profile for a Tenant Administrator. This ensures that it is never possible for any user to hi-jack system access by, for example, changing another user’s email address, or resetting their password.
Note that there is an email validation process whereby users are not able to change an email address without validating through their own email address.
An Explicit Roles is explicitly allocated to Users. Most of the Roles in the system are Explicit.
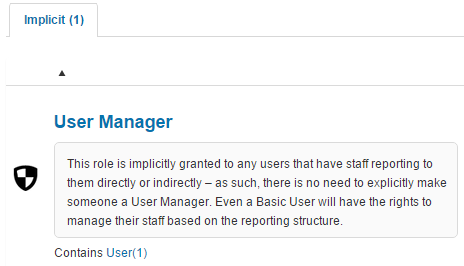
An Implicit Role is a Role that is automatically assigned to Users when they have staff reporting to them. There is one Implicit Role in the system, User Manager. See the document on Position Management for further information on User reporting.
1300 857 687 (Australia)
+61 2 6652 9850 (International)
ACN 091 302 975
ABN 35 081 897 494
© 2024 Janison
Janison acknowledges the traditional owners of the land on which we work and meet. We acknowledge the continuous care of the land, animals and waterways. We pay our respects to Elders past, present and emerging.